ConfigMaps & Secrets Persistent Volumes (PV) & Persistent Volume Claim (PVC)
ConfigMaps :-
A ConfigMap is an API object used to store non-confidential data in key-value pairs. Pods can consume ConfigMaps as environment variables, command-line arguments, or as configuration files in a volume. It allows you to decouple environment-specific configuration from your containerized application, making your application more portable. ConfigMap does not provide secrecy or encryption. If the data you want to store are confidential, use a Secret rather than a ConfigMap.
Secrets :-
Secrets, as the name suggests,A Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. Use Cases for Secrets: Storing database credentials, API tokens, SSL certificates.
Kubernetes objects are entities in a Kubernetes cluster that represent the cluster’s state
deployment.yml file
apiVersion: apps/v1
kind: Deployment
metadata:
name: mysql-deployment
namespace: mysql
labels:
app: mysql
spec:
replicas: 2
selector:
matchLabels:
app: mysql
template:
metadata:
labels:
app: mysql
spec:
containers:
- name: mysql
image: mysql
ports:
- containerPort: 3306
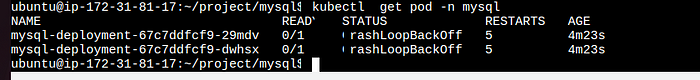
because we can’t created database so out mysql creash every time when it’s created.
Creating a ConfigMap:
You can create a ConfigMap using a YAML file or directly from the command line. Here’s an example using a YAML file:
Create configmap.yml file
apiVersion: v1
kind: ConfigMap
metadata:
name: mysql-config
namespace: mysql
labels:
app: mysql
data:
MYSQL_DATABASE: 'cooldb'
Apply it with:
kubectl apply -f configmap.yml -n config-secret
kubectl get configmaps -n config-secret //checking the status of the ConfigMaps
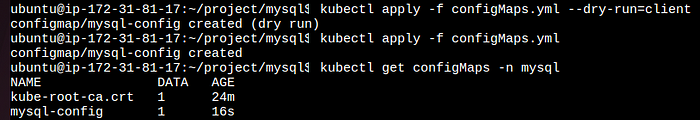
deployment.yml file after Create configmap.yml file (database)
1`spec:
replicas: 2
selector:
matchLabels:
app: mysql
template:
metadata:
labels:
app: mysql
spec:
containers:
- name: mysql
image: mysql
ports:
- containerPort: 3306
env:
# Define the environment variable
- name: MYSQL_DATABASE # Notice that the case is different here
# from the key name in the ConfigMap.
valueFrom:
configMapKeyRef:
name: mysql-config # The ConfigMap name,value comes from.
key: MYSQL_DATABASE # The key to fetch.
This time it also give error because we don’t give pasword in mysql database.
Creating a Secret:
Before we create a secret, we need to create a base64 encoded string of the database password that we will use in our deployment.yml file.
I’m taking the following details as secret key. Following details as secret key:
Password:test123
echo -n 'test123' | base64
For verifying the secret key, we can use the following command:
echo -n 'dGVzdDEyMw==' | base64 --decode
secret.yml file
apiVersion: v1
kind: Secret
metadata:
name: mysql-secret
namespace: mysql
labels:
app: mysql
type: Opaque
data:
MYSQL_PASSWORD: dGVzdDEyMw==
What is the Opaque type? : The opaque type is used to store sensitive data such as passwords, certificates, and tokens.
Apply the updated deployment using the command:
kubectl apply -f secret.yml -n config-secret
kubectl get secrets -n config-secret
deployment.yml file after Create secret.yml file (password)
apiVersion: apps/v1
kind: Deployment
metadata:
name: mysql-deployment
namespace: mysql
labels:
app: mysql
spec:
replicas: 2
selector:
matchLabels:
app: mysql
template:
metadata:
labels:
app: mysql
spec:
containers:
- name: mysql
image: mysql
ports:
- containerPort: 3306
env:
# Define the environment variable
- name: MYSQL_DATABASE # Notice that the case is different here
# from the key name in the ConfigMap.
valueFrom:
configMapKeyRef:
name: mysql-config # The ConfigMap this value comes from.
key: MYSQL_DATABASE # The key to fetch.
- name: MYSQL_ROOT_PASSWORD
valueFrom:
secretKeyRef:
name: mysql-secret
key: MYSQL_PASSWORD
kubectl apply -f deployment.yml -n config-secret
kubectl get pods -n config-secret
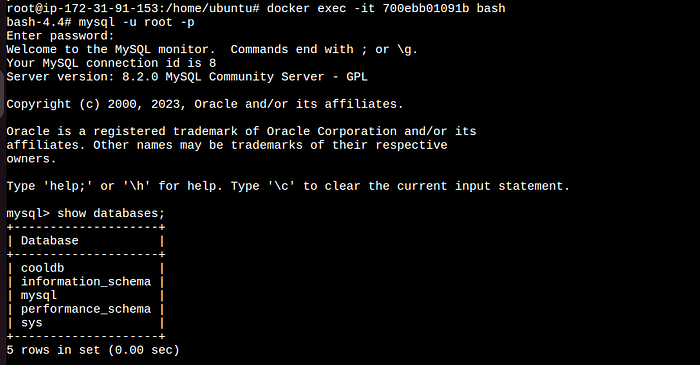
worker node :
here we can see inside the container a database created.
Persistent Volumes (PV)
Persistent Volumes are resources in Kubernetes that provide storage implementations, such as NFS, iSCSI, or cloud-specific storage systems like AWS EBS, GCE Persistent Disk, and Azure Disk. A PV has a lifecycle independent of any individual Pod that uses the PV. This means the data remains intact, even when no Pod is using it.
Persistent Volume Claim (PVC)?
A PVC is a request for storage by a user. It’s similar to a Pod: while Pods consume node resources, PVCs consume PV resources. Once a PVC is bound to a PV, it can be mounted to a Pod and utilized as a regular disk.
Creating a Persistent Volume:
Here’s a basic example of a PV that provides 1Gi of storage on a local node:
apiVersion: v1 kind: PersistentVolume metadata: name: my-pv namespace: mysql spec: capacity: storage: 1Gi volumeMode: Filesystem accessModes: - ReadWriteOnce hostPath: path: "/home/ubuntu/volume"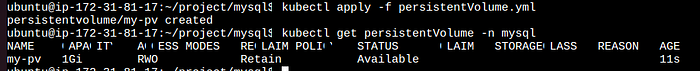
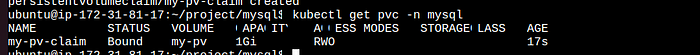
2. Creating a Persistent Volume Claim:
A PVC will claim storage from the available PVs. Here’s an example:
kind: PersistentVolumeClaim metadata: name: my-pv-claim namespace: mysql spec: accessModes: - ReadWriteOnce resources: requests: storage: 500MiOnce the above PVC is created, Kubernetes will bind it to a suitable PV.
Deployment.yml file
apiVersion: apps/v1 kind: Deployment metadata: name: mysql-deployment namespace: mysql labels: app: mysql spec: replicas: 2 selector: matchLabels: app: mysql template: metadata: labels: app: mysql spec: containers: - name: mysql image: mysql ports: - containerPort: 3306 env: # Define the environment variable - name: MYSQL_DATABASE # Notice that the case is different here # from the key name in the ConfigMap. valueFrom: configMapKeyRef: name: mysql-config # The ConfigMap this value comes from. key: MYSQL_DATABASE # The key to fetch. - name: MYSQL_ROOT_PASSWORD valueFrom: secretKeyRef: name: mysql-secret key: MYSQL_PASSWORD volumeMounts: - name: mysql-persistent-storage mountPath: /var/lib/mysql # container path volumes: - name: mysql-persistent-storage persistentVolumeClaim: claimName: mysql-pv-claim